Crack Nt Hash Windows 7
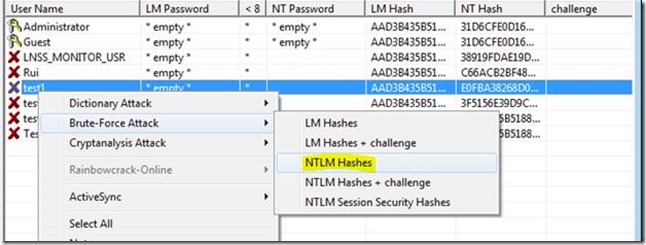
Extracting the hashes from the SAM (locally) If LM hashes are enabled on your system (Win XP and lower), a hash dump will look like: Administrator:500:01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A8287::: If LM hashes are disabled on your system (Win Vista, 7, 8+), a hash dump will look like: Administrator:500:NO PASSWORD.:0CB6948805F797BF2A8287::: The first field is the username. The second field is the unique Security IDentifier for that username. The third field is the LM hash and the forth is the NTLM hash.
Free XP Rainbow tables. These tables can be used to crack Windows XP passwords (LM hashes). They CANNOT crack Windows Vista and 7 passwords (NT hashes). If you want to crack NT hashes as found on Windows Vista by default (the LM Hash column is always empty on the ophcrack main window). If you want to crack NT hashes as found on Windows Vista by default (the LM Hash column is always empty on the ophcrack main window).
Example with fgdump. Double click on fgdump.exe you've just downloaded,. After a few seconds a file '127.0.0.1.pwdump' has been created.
Crack Nt Hash Online
Edit this file with notepad to get the hashes. Copy and paste the hashes into, and we'll crack them for you. On Linux (or Live system such as ) you can use (python based), or Samdump2: bt # samdump2 /mnt/XXX/WINDOWS/system32/config/system /mnt/XXX/WINDOWS/system32/config/sam samdump2 2.0.1 by Objectif Securite (original author: ncuomo@studenti.unina.it Administrator:500:01fc5a6be7bc6929aad3b435b51404ee:0cb6948805f797bf2a8287::: You can then post the hashes to in order to get the plain text. Extracting Windows Password hashes remotely Man In the Middle attack You can use and the man in the middle attacks to sniff the username and password of a user over the network. You can read.
There so much that ettercap can do and there are many tutorials covering how to use it! Metasploit / hashdump is an interesting pentest framework. Documentation is. Once you have compromised the computer using metasploit you can extract the hashes doing: use priv hashdump Dump Tools or can also remotely dump hashes: C: fgdump.exe -h 192.168.0.10 -u AnAdministrativeUser -p password or C: pwdump6.exe -u AnAdministrativeUser -p password 192.168.0.10 Here, AnAdministrativeUser's account will be used to perform the password dump. Keep in mind that any user used to perform password dumps needs administrative credentials. In this scenario, you will be prompted for the password before the password dump starts. Fgdump hashes are stored in.pwdump file; pwdump6 will dump the SAM to the screen.
You can then post the hashes to in order to get the plain text.
Nt Hash Decoder
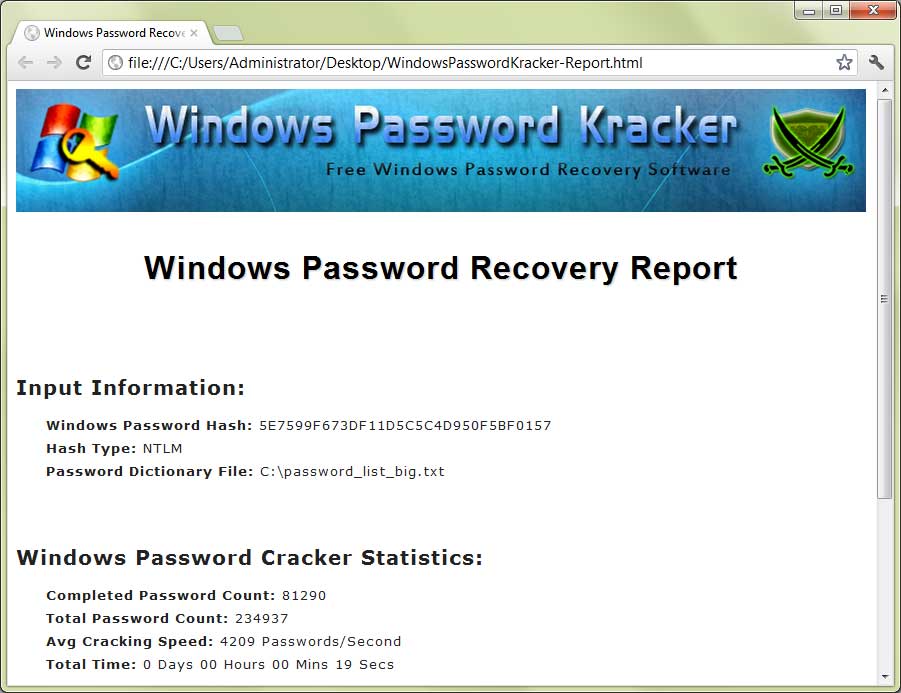
How CrackStation Works CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash.
If the hash is present in the database, the password can be recovered in a fraction of a second. This only works for 'unsalted' hashes. For information on password hashing systems that are not vulnerable to pre-computed lookup tables, see our. Crackstation's lookup tables were created by extracting every word from the Wikipedia databases and adding with every password list we could find.
Nt Hash Tables
We also applied intelligent word mangling (brute force hybrid) to our wordlists to make them much more effective. For MD5 and SHA1 hashes, we have a 190GB, 15-billion-entry lookup table, and for other hashes, we have a 19GB 1.5-billion-entry lookup table. You can download CrackStation's dictionaries, and the lookup table implementation (PHP and C) is available.